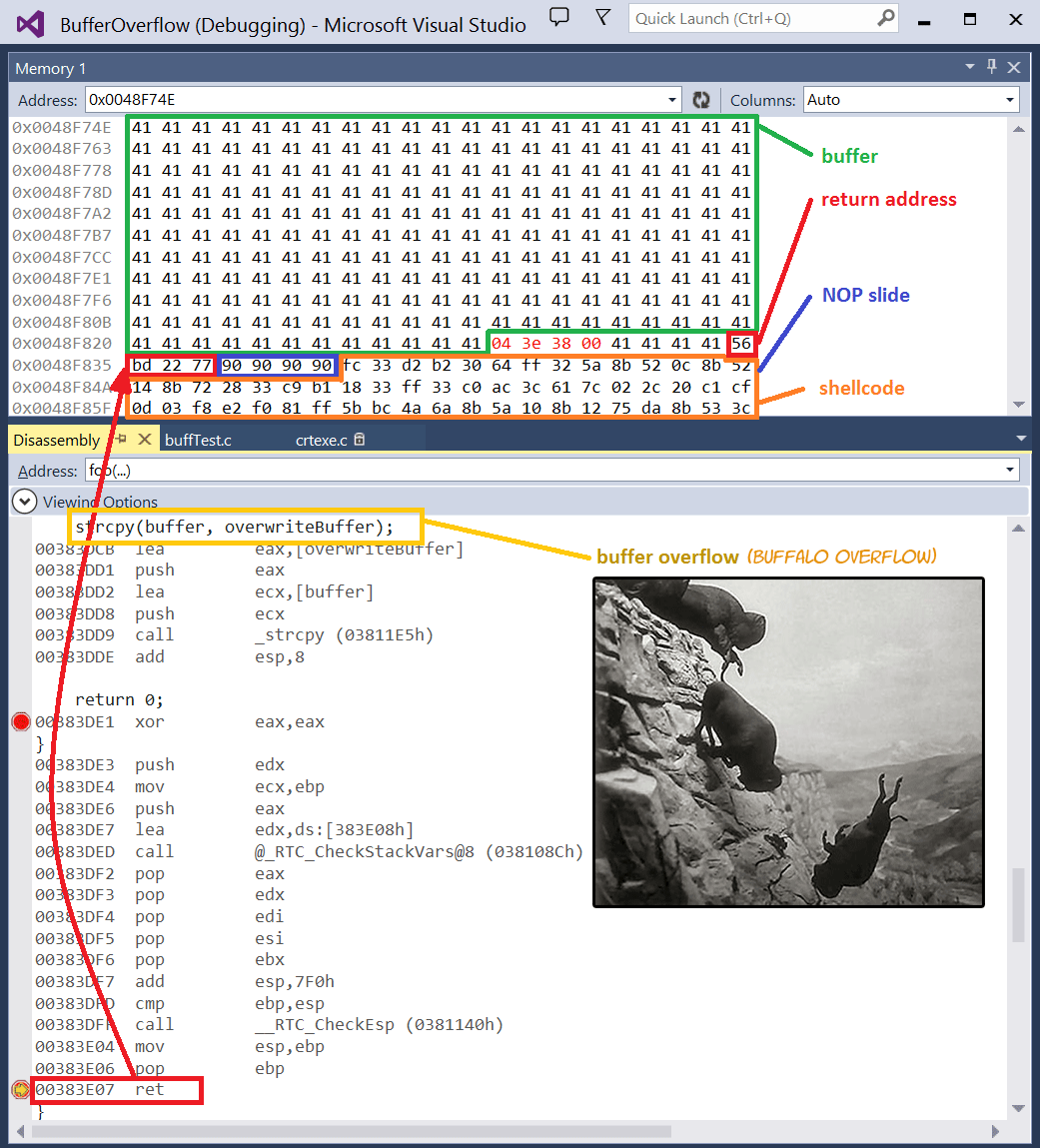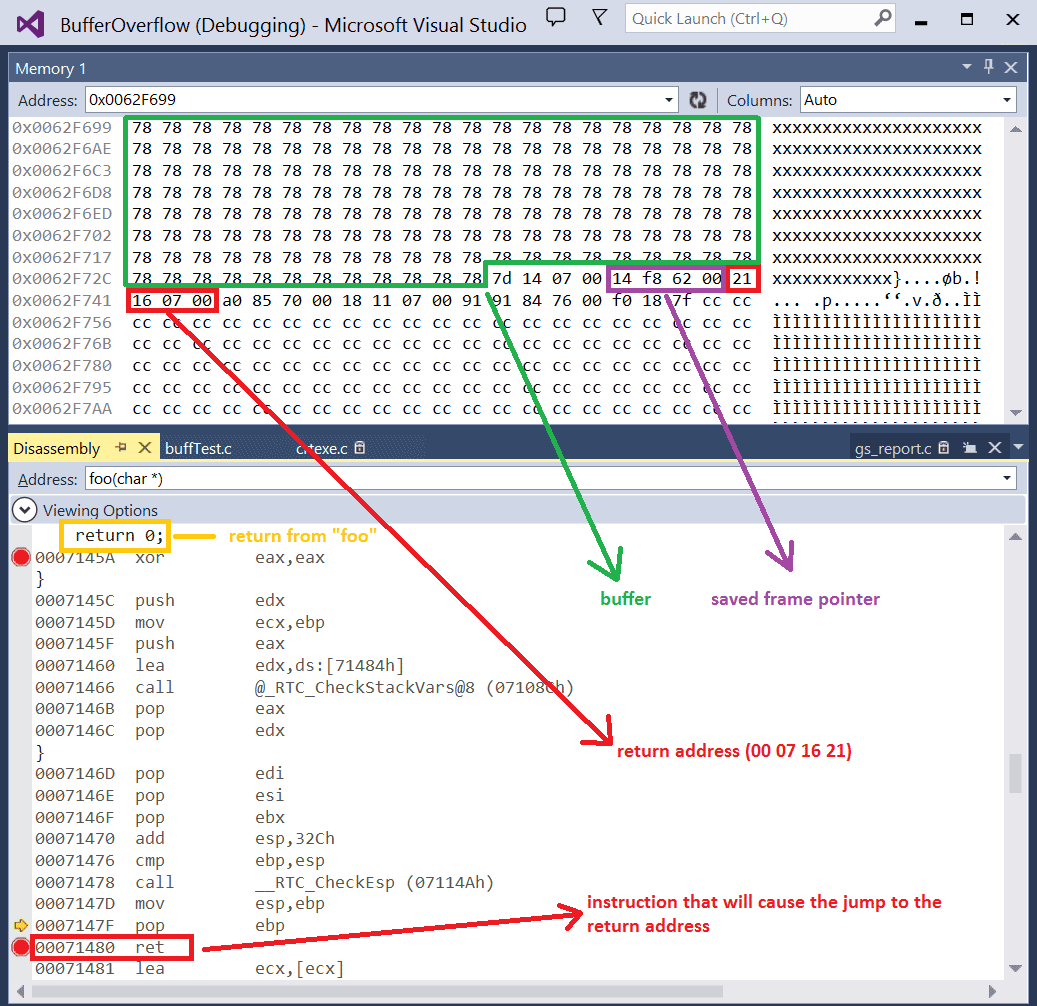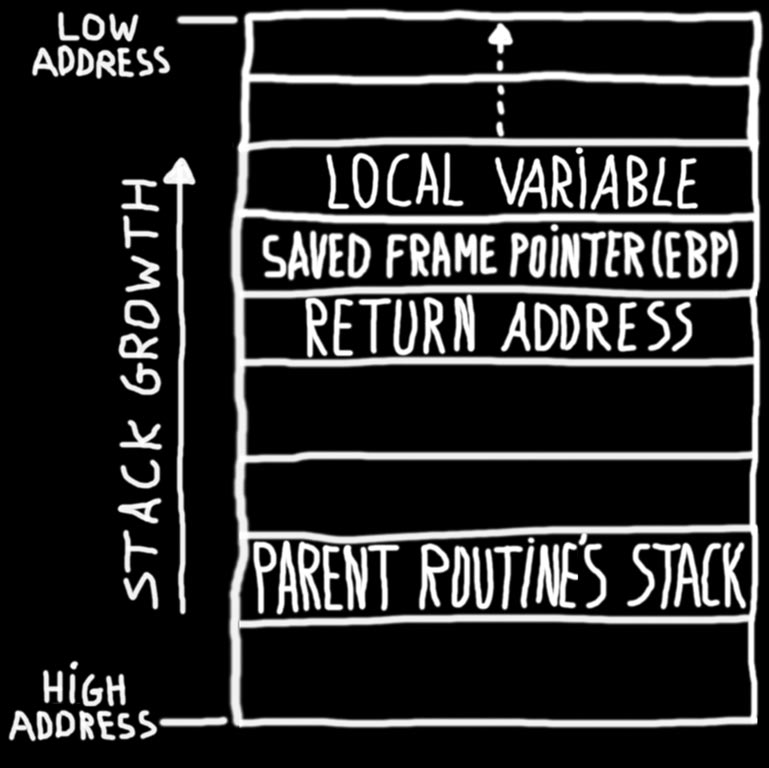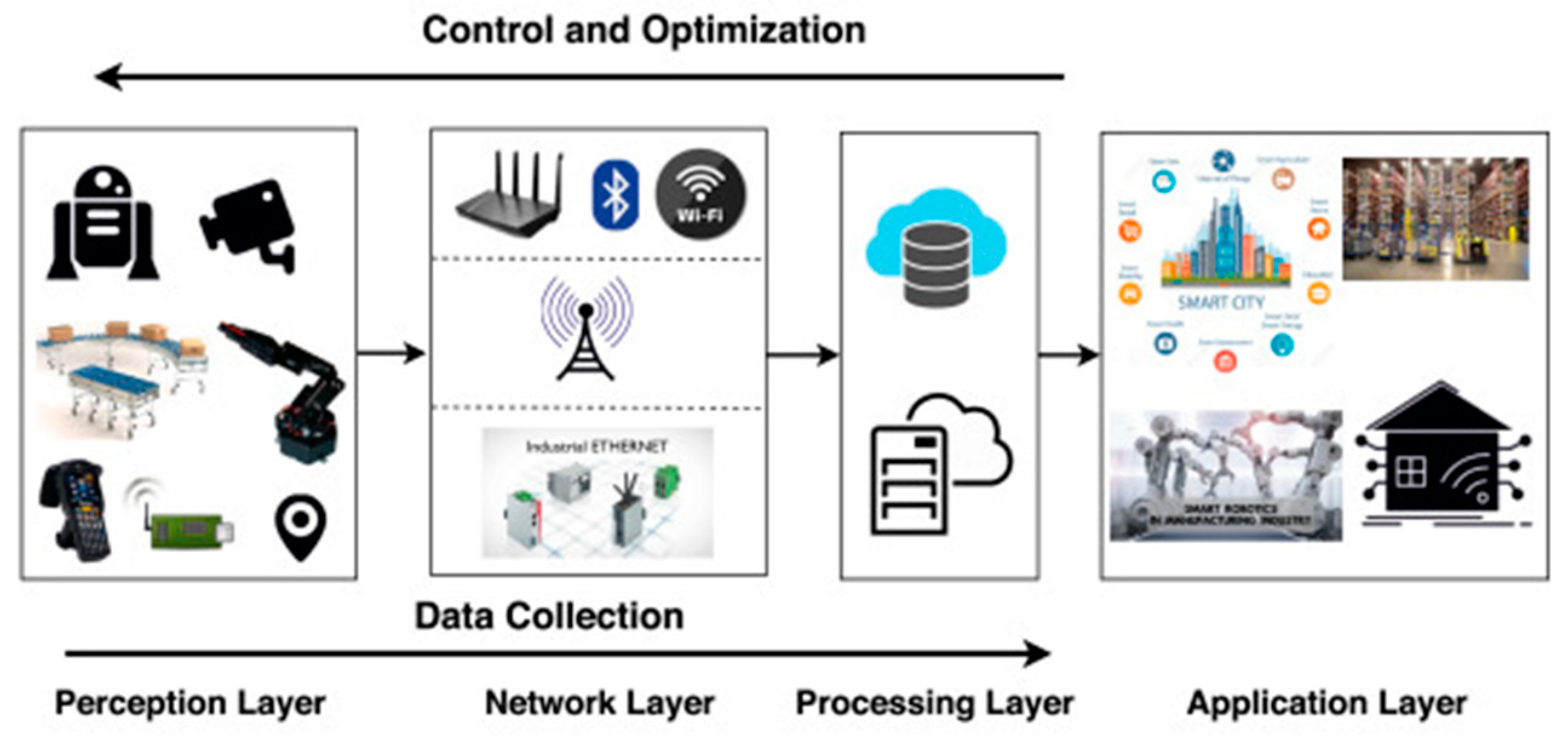
Buffer Overflow Network Security Computer Network Attack, PNG, 1240x1346px, Buffer Overflow, Area, Attack, Computer Network, Computer

SUNY at Buffalo; Computer Science; CSE620 – Advanced Networking Concepts; Fall 2005; Instructor: Hung Q. Ngo 1 Agenda Last time: finished brief overview. - ppt download

Overflow Conference (Buffalo) Recap | What a move of God we experienced in buffalo, New York! Thank you Curtis N Ani Minniefield and Sword of the Spirit Ministries for allowing us to